More and more areas of human activity are going digital: from learning to business and work. Accordingly, the level of user security on the Internet and in the digital space must improve.
And today we will discuss with you the risks and threats to mobile app security. There are indeed many of them, but we will highlight the main ones, and some of them will be analysed in detail. Among the main risks to the app and companies, the most frequent ones are:
- hacking attempt to steal information;
- a hacking attempt to steal data and customer databases;
- attempted cyberattacks to destroy data;
- attempts to hack into user accounts for fraudulent purposes;
- viruses.
According to statistics, nearly 4 billion people around the world use smartphones. And each of them can be affected by attackers. Recently, attacks on services and applications have become more frequent. In addition to viruses and the simplest phone scams asking for confirmation of a "left-handed" payment, there are several key types of attacks and scams.
Cross-Site Request Forgery (CSRF)
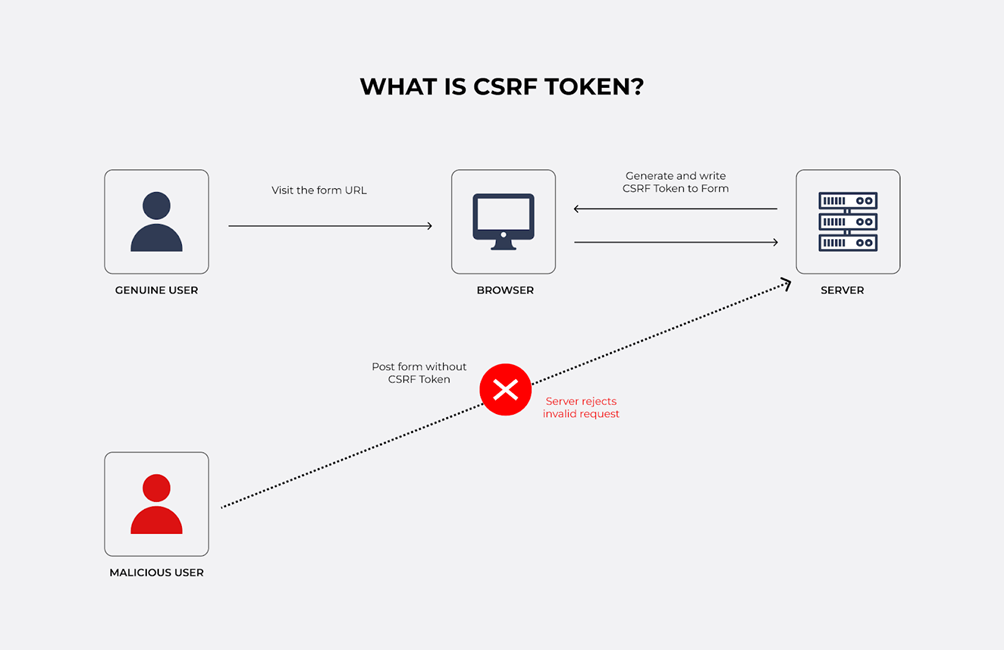
CSRF is one of the most common types of fraud over the past few years. With the growth of the digital sales industry, there are more instances of these schemes occurring. What is the essence of this system:
- a customer (John) goes to a website that has been created by an attacker;
- the attacker (or script) sends a request to another server (in our case, a payment system) on John's behalf;
- the attacker performs a malicious action — withdrawal of funds to his account;
- the payment service sends a request for transaction verification to John;
- John's confirmation;
- the payment system sees that the payment is verified and makes it;
- only the money goes not to John, but to the fraudster.
HTTPS-based sites are highly vulnerable to this fraud system. Other manipulations can include: changing the password, secret question, password recovery or re-binding the phone number, adding a new administrator and other actions that imply any changes on the servers
Is it possible to protect against this format of attack? Yes, it is.
Choose a Secure Framework
Use a secure framework, for example, "NET". It has a built-in system of protection against such attacks. Further customization of the framework will only improve security.
Anti-CSRF Tokens
Tokens are used if your framework has no protection against CSRF attacks. The essence of the system is that the browser generates a unique token for each user and checks for its presence after each request from the user.
The token must fulfil the following conditions:
- uniqueness within each transaction;
- one-time use;
- resilient size to tampering;
- cryptographic generation by a persistent pseudorandom number generator;
- limited validity period.
Using Two Tokens at Once
The tokens are still the same, only now there are two of them. The point of this security strategy is as follows:
- one token is stored in the cookie;
- the second token is stored in the response parameters;
- if the server receives an insecure request, it checks two tokens.
Use of the Same-Site Flag in Cookies
The role of this flag is to flag a cookie of a particular domain. The source is flagged for later checks, so attackers will not be able to fulfil requests from left sites.
The flag is supported by almost all browsers and is an important attribute of the user's security system.
Require confirmation from the user. For such operations as transferring funds or changing a password, add another action from the client's side: select traffic lights or motorbikes in pictures, enter captcha and so on. Users don't like it, but they'll be protected.
Buffer Overflow Attacks
Buffer overflow is a phenomenon that occurs when a programme writes data beyond the allocated buffer space in memory.
Causes of problems:
- improper handling of data that is received externally;
- no normal protection from the subsystem (compiler or interpreter).
As a consequence, data that is located next to or before the buffer may be corrupted or lost.
Buffer overflow is one of the most frequent variants of system hacking. This is because most high-level languages use a stack frame. Programme data is mixed with control data.
If a buffer overflow occurs, the programme may be closed in crash mode or simply hang.
If an overflow occurs in a stack frame, attackers can access the code and load it with the privileges of the account from which the program was run.
How Do You Prevent Attacks and Disruptions?
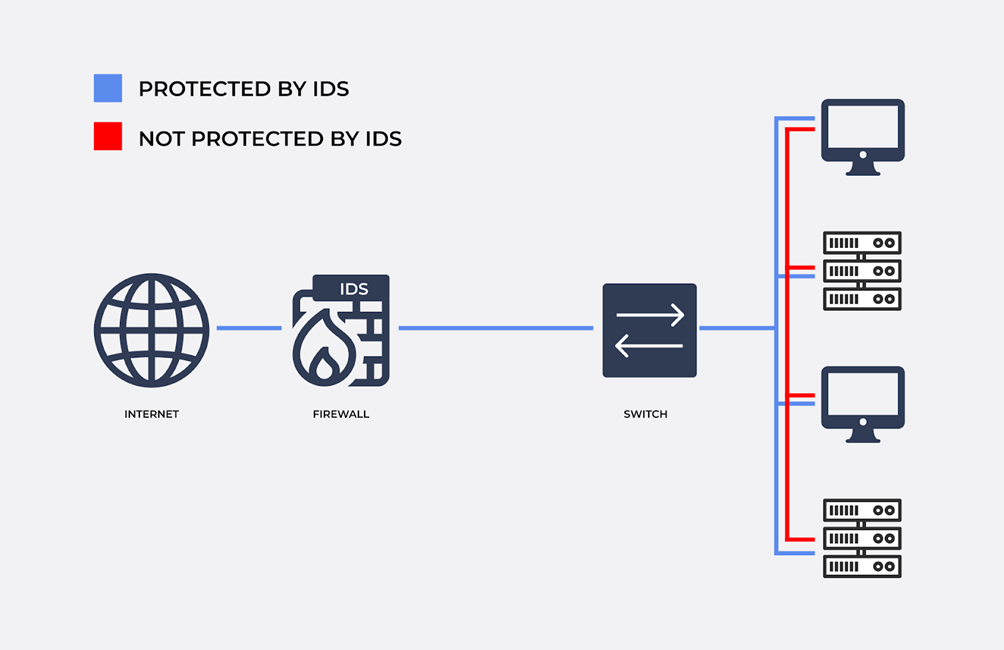
Intrusion Detection Systems
There are a number of intrusion detection systems (IDS). They help to detect and prevent attempts to remotely exploit and access the buffer.
In buffer tampering, crooks use data with a long array of instructions, IDSs block such packets.
Stack Corruption Protection
Used to detect the most frequent buffer overflow errors. It is important to check that the call stack has not been modified before returning from a function. If it was still modified, the programme terminates execution with an error.
Executable Code Space Protection for Unix-Like Systems
Executable code space protection can help here. Address space randomization or options to deny simultaneous memory accesses for execution and writing are used. A stack that is not executable prevents most shell code exploits.
Executable Code Space Protection for Windows Systems
There are a number of solutions for Windows-based systems, both from the developers themselves and from third-party brands.
Microsoft has several offerings: Data Execution Prevention or DEP, as well as a separate stack protection mechanism. The stack is tagged using "whistleblowers" and their integrity is then verified. If a whistleblower has been changed, the stack is corrupted.
Use Safe Libraries
It is often encountered in C/C++ languages because they do not hide the details of representing buffers as data type containers.
In such a situation, you should use abstract data type libraries. They perform central automatic management of buffers. They also have a buffer overflow checker.
Regular Application Updates to Fix Security Vulnerabilities
Application updates. Are they necessary? And why do we get alerts so often that software is out of date or a new version has been released?
Yes, few people like pop-up alerts about a new update or a reminder that it's time to upgrade. Sometimes updates are released right in the middle of a game session, which is "loved" by players and users, but it's an important point that shouldn't be ignored.
It just so happens that hackers quickly adapt to new security formats and protocols.
Therefore, developers regularly have to work on security, "patch holes" and improve it. Here are some reasons and examples that demonstrate the need for regular app updates for the user.
Ensuring the Highest Level of Protection
No matter how much an app is tested before release, there will still be minor inaccuracies or bugs that need to be fixed or eliminated after launch. If this is not done, through such gaps in protection, fraudsters often try to hack into the application, user accounts and steal databases, finances, information. It is updates that help prevent them from occurring.
Security of Devices With Family Access
Ecosystems have become more affordable over the past few years. More and more people are putting in a smart home or digital security system devices (e.g. smoke, water, motion sensors, etc.). These are all linked into a single system and family members have access to an app to monitor the status of all devices and the home.
If apps are not updated, sooner or later hackers will be able to access your home's controls, unlock locks or disable alarms with cameras.
Improved Performance
Software updates affect the performance of devices as well. Over time, the app is "polished" to a perfect state, optimized for the device and provides better performance with less use of smartphone resources.
Adding New Functionality
Updates bring not only fixes, but also improvements and new functionality. The simplest example would be access to payment confirmation in mobile banking through the use of biometrics. Here you will find both new functionality and improved security.
Company Security
Updating the application is mandatory not only to protect the user, but also the company itself. In most cases, management allows the software to be installed on personal smartphones (here we return to the common vulnerabilities of phones and applications that are not updated). When attackers gain access to the smartphone files, they will be able to access the work application as well, causing damage to the company.
Conclusions
Having your own app is an important part of e-commerce business. But a poor quality app with security vulnerabilities can jeopardize a company. That's why it's so important to focus on app security and integrating up-to-date data protection systems during the app development stages. During the app development process, it is important to use all current testing methods and tools.